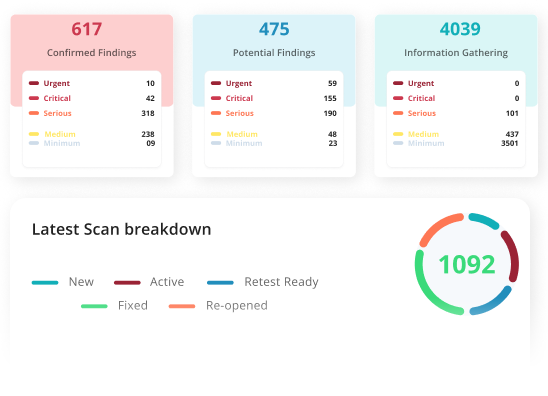
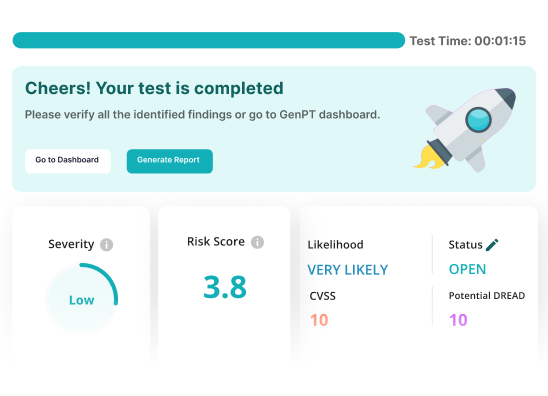
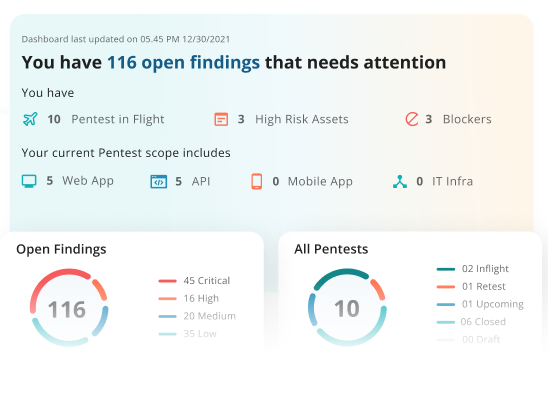
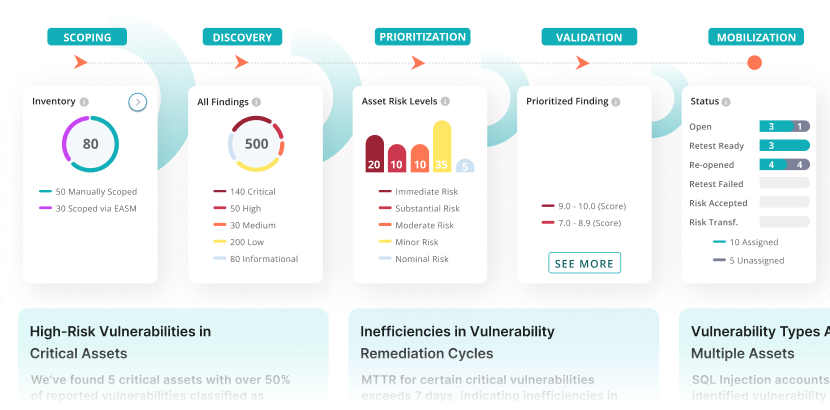
Continuous Pentesting & Threat Exposure Management At Scale
.webp?width=1856&height=1158&name=HomePage-Banner%20(1).webp)
Expert-led penetration-testing, autonomous DAST, and real-time attack surface mapping. Everything you need in one CTEM platform to discover, prioritize, and fix critical vulnerabilities.
Trusted by






News
Siemba Recognized in 2025 Gartner® Hype Cycles™ for Security Operations, Application Security, and Everything as a Service (XaaS)
.webp?width=2000&height=1434&name=Figure1%20(1).webp)
“We are proud to be recognized for the second consecutive year across three Gartner® Hype Cycles™ reports. We believe this is a strong validation of our thesis that continuous validation and visibility are critical to modern cybersecurity.”
Kannan Udayarajan, Founder & CEO, Siemba
.webp?width=2000&height=1434&name=Figure1%20(1).webp)
Impact You Can Count On
Unify security capabilities, amplify impact and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.
Alex Chriss
Chief Technology Officer
Venmo
Full Funnel Security Begins Here
Weave Cybersecurity Into Your Operational DNA
Map attack surfaces with precision, automate vulnerability discovery, and prioritize remediation effortlessly, at any scale. Supercharge your response to emerging threats and stay ahead of attackers. The outcome? Streamlined operations, faster threat mitigation and a stronger security posture with minimized risk.
Introducing
Unleash the Power of AI-Driven Strategic Insights
Shift your conversations from chasing vulnerabilities to mitigating true risk. AISO gives you deep security insights in real time to drive efficiencies, accelerate threat remediation and maximize your return on mitigation (RoM).
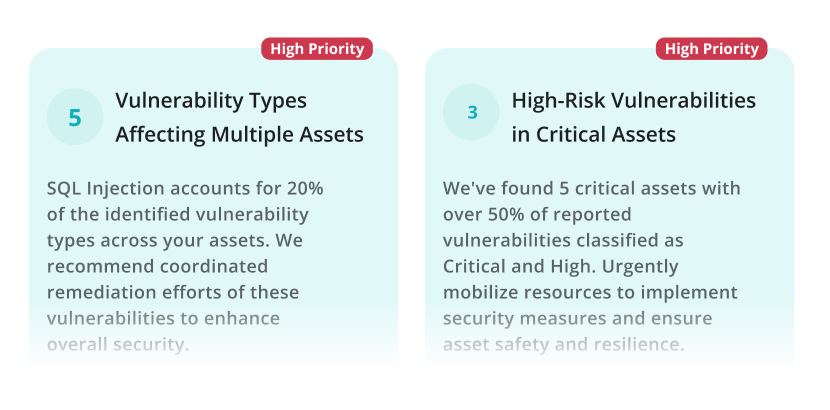
Imminent SSL/TLS Certificates Expiry
8 SSL/TLS certificates will expire in the next 30 days, which could lead to service disruptions and security risks. Timely renewal of these certificates is critical to maintaining secure and seamless communications.
Inefficiencies in Vulnerability Remediation Cycles
MTTR for certain critical vulnerabilities exceeds 7 days, indicating inefficiencies in your current remediation processes. Streamlining these processes can expedite vulnerability resolution, minimizing exposure.
Unrestricted Hacker Access Through Unpatched Exploits
18 vulnerabilities allow unauthenticated exploitation and have public exploits available. The combination of high severity, remote access risk, and available exploits makes these vulnerabilities particularly dangerous.
Zero-Day Vulnerabilities Jeopardize Security
Multiple unpatched vulnerabilities have been identified, potentially granting attackers unauthorized access to critical systems. The absence of compensating controls significantly increases the organization's exposure to cyber threats.
Vulnerabilities Lacking Patches Pose Immediate Risk
A significant number of active vulnerabilities have been identified for which patches are currently unavailable. These critical vulnerabilities are increasing the potential attack surface and risk exposure.
Vulnerabilities Enable Lateral Movement or Privilege Escalation
Among the newly identified vulnerabilities, a significant number allow lateral movement across systems and privilege escalation, posing severe risks to the organization's security posture.
Enterprise Cybersecurity:
Protecting Every Touchpoint and Role
Siemba supports each team with real-time protection, streamlined compliance, and scalable security built for the pace of your modern enterprise.
Defend Smarter. Choose Siemba.
Discover proactive defense at its best with our AI-powered full-funnel offensive security platform. Secure what matters most.
Integrations to enable Highest Availability and Horizontal Scalability
.gif?width=1363&height=533&name=Integrationsforsiembaplatform-ezgif.com-optimize%20(1).gif)
Success Stories From Our Clients
.png?width=380&height=378&name=image%20(58).png)
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Success Stories
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation
“Unify security capabilities, amplify impact, and strengthen resilience. Here’s why leading organizations trust Siemba to proactively defend against evolving threats.”
Huno
Company, Designation
Committed to Excellence
We Understand Your Industry’s Intricacies
At Siemba, we recognize that cybersecurity goals and obstacles morph across various sectors. Our solutions bow to your needs.
Highlights from Siemba
.webp?width=288&height=187&name=blog%20(288%20x%20187%20px).webp)



.png)